Monitoring System Activity
The Log Tracker provides a central location for the review and analysis of system activity. The back-end servers and databases that store information used in Engage record system events as log entries. These entries are collected and displayed in the Log Tracker.
Use the Log Tracker to identify the users and automated processes that are responsible for system events. You can use this information for troubleshooting and problem-solving. You can also find times when your system is less active and has the capacity to process resource-intensive tasks.
Views
The Log Tracker gives you three different views of the events that have taken place in your system. Each provides a different level of detail.
The Overview gives you the ability to compare the number of current log entries with the average number over the same time frame. This helps you easily detect abnormal system activity.
The Chart View shows you entries over time. Each entry type is shown as a line on the chart. This helps you see exactly when specific events take place in your system and how often they occur.
The List View lets you see detailed information for all the events that have taken place in your system. This helps you identify the source of each event and provides reference IDs that help you find and manage related objects in your system.
Together, these views help you identify trends and isolate problems.
Processes in the Log Tracker
The Log Tracker displays a record of a range of system events, including entries related to ongoing system processes. For a process, the Log Tracker shows an entry that records the start event and a second entry that records the completion. The Log Tracker does not allow you to interact with a process. To interact with an ongoing process, use the Process Overview window. For more information, see Processes.
Security
The Log Tracker helps you identify security-related incidents. This includes attempts to access the system using compromised user accounts as well as the identification of actions taken by a non-user who successfully infiltrates the system.
The Access entry class includes all entries related to user login events, including both successful and unsuccessful login attempts. A higher-than-average number of unsuccessful login attempts can indicate one of the following situations:
A user has forgotten the password associated with their Engage account.
A non-user is attempting to gain access to your system using the credentials of an existing user account.
Example
A system administrator opens the Log Tracker Overview window. She notices that the number of recent events in the Access category is far higher than average.
She clicks the Access column to view the events for this category in the Log Tracker Chart View window. The line that represents failed login attempts shows several entries beginning around midnight. The system shows the same number of failed login attempts over the course of several hours.
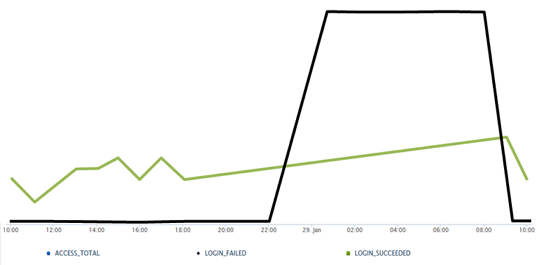
The system administrator clicks the point on the chart for the first recorded failed login. All of the log entries for the Access class are displayed in the Log Tracker List View. Here, she sees that the account used changes after every third failed login. The last entry in the Access class has the label LOGIN_SUCCEEDED. This could indicate that, after several attempts with incorrect login credentials, an intruder was able to log into the system.
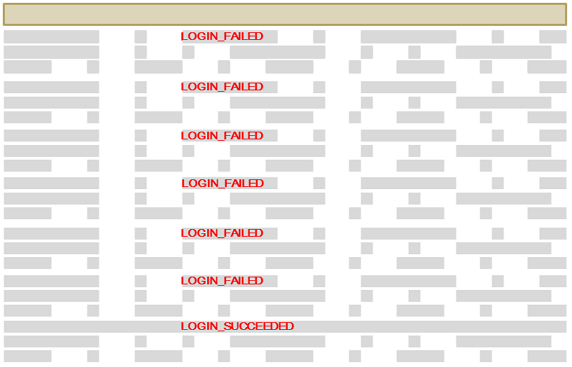
The system administrator speaks with the owner of the account and confirms that the login was not attempted by the account owner. She goes back to the List View and enters the email address in the Identifier filter, and displays only entries related to this user.
She expands the filter to include all entry categories and finds any changes made by this account after logging in. Using the information collected from the Log Tracker, she identifies and reverts changes made by the intruder. She informs the owner of the account of these changes and asks him to change his password.